Hackers are targeting victims with fake broken Google Meet calls in an attempt to infect them with malware and thus take over their sensitive information, experts have warned.
A report from cybersecurity researchers Sekoia claims that the campaign is a new variant of the previously observed ClickFix attack.
ClickFix victims are shown a fake error page (e.g. a browser is outdated and therefore unable to open a certain website) and then offered a solution (a 'patch' or 'update'). version'). If victims do not realize the trick and download the “fix”, they end up infecting their terminals with other malware.
StealC and Rhadamanthys
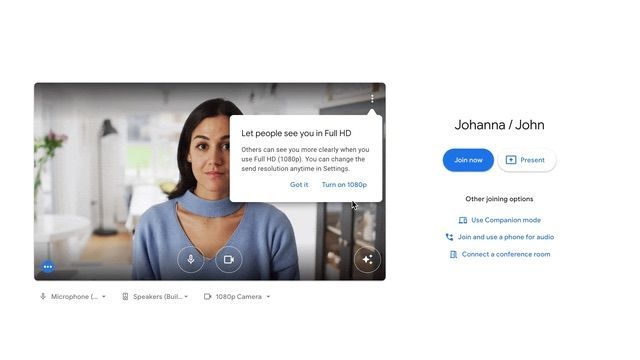
In this case, Sekoia researchers found several websites purporting to be Google Meet video conferencing landing pages.
People who open these websites are shown an error related to their microphone or camera. The 'solution' offered is a PowerShell code, copied to the clipboard, which runs in the Windows command prompt.
Ultimately, this code implements the StealC or Rhadamanthys information stealer. For macOS, which is also the target, attackers remove AMOS Stealer as a .DMG file named “Launcher_v194”.
The threat actors in this campaign are called Slavic Nation Empire (SNE) and Scamquerteo, apparently subgroups of other threat actors called Marko Polo and CryptoLove, respectively.
In addition to Google Meet, Sekoia has discovered that Zoom, PDF readers, fake video games (Lunacy, Calipso, Battleforge, Ragon), web3 browsers and projects (NGT Studio), and messaging applications (Nortex) are abused for the same purpose.
The attack will most likely start with a phishing email and primarily target transportation and logistics companies.
Through beepcomputer