Millions of secrets and authentication keys were leaked on GitHub in 2023, and most developers didn't mind revoking them even after being notified of the mishap, new research claims.
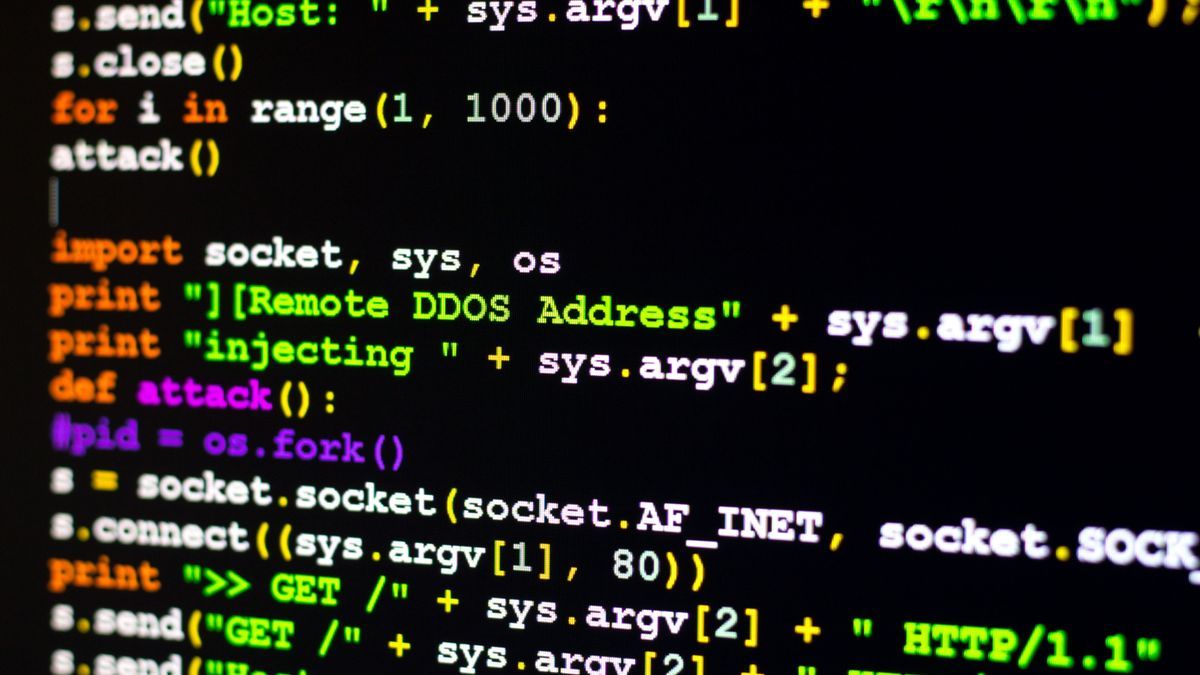
A report from GitGuardian, a project that helps developers protect their software development with automatic secret detection and remediation, states that in 2023, GitHub users accidentally exposed 12.8 million secrets across more than 3 million repositories. public.
These secrets include account passwords, API keys, TLS/SSL certificates, encryption keys, cloud service credentials, OAuth tokens, and the like.
Slow response
During the development stage, many IT professionals would code different authentication secrets to make their lives easier. However, they often forget to remove secrets before publishing the code to GitHub. Therefore, if any malicious actor discovers these secrets, he will gain easy access to private resources and services, which can lead to data breaches and similar incidents.
India was the country where the most leaks originated, followed by the United States, Brazil, China, France and Canada. The vast majority of breaches came from the IT industry (65.9%), followed by education (20.1%). The remaining 14% were divided between science, retail, manufacturing, finance, public administration, healthcare, entertainment and transportation.
Anyone can make a mistake and encrypt secrets, but what happens next is perhaps even more worrying. Only 2.6% of secrets are revoked within an hour; virtually everything else (91.6%) remains valid even after five days, when GitGuardian stops tracking its status. To make matters worse, the project sent 1.8 million emails to different developers and companies, warning them of its findings, and only 1.8% responded by removing the secrets from the code.
Riot Games, GitHub, OpenAI and AWS were listed as companies with the best response mechanisms.
Through beepcomputer