Frankly, it has been a terrible week for those who work in the healthcare sector. Several different healthcare organizations have suffered ransomware attacks, each with widespread ramifications. This occurs when attackers lock sensitive data and hold it hostage until the organization pays a ransom.
The U.S. Department of Health and Human Services (HHS) Office for Civil Rights (OCR) has reported a 264% increase in ransomware incidents reported during the last five years. Given the large amount of data that healthcare companies must collect and store, as well as the often sensitive nature of this data, this is not surprising. This data makes healthcare organizations a prime target for extortion, and hackers have absolutely taken advantage of this.
This has been especially seen in the last week alone, when several different healthcare organizations around the world were either affected by their ransomware attacks or released more information about them.
Mental health data exposed in NHS ransomware attack
On 7 May, NHS Dumfries and Galloway confirmed that a large amount of personally identifiable information belonging to both staff and patients had been published on the dark web. This data included information about the children's mental health and was leaked following a ransomware attack launched against the organization.
The cyberattack took place on March 15 after a ransomware gang hacked into NHS Dumfries and Galloway's computer system and stole a large amount of data.
After the attack, hackers began leaking the data on the dark web as “proof” that it had been stolen, with the promise that more would be leaked if the ransom was not paid. This has also resulted in the leaking of children's mental health data in an “absolutely abhorrent criminal act” in the words of NHS Dumfries and Galloway chief executive Julie White.
Due to the amount of data stolen, thousands of people could be affected.
Ascension hospital network taken down by cyber attack
In the United States, ransomware also attacked healthcare organizations. On May 8, a serious cybersecurity incident was reported that affected the Ascensión hospital network.
The hospital's entire system was reportedly down during the incident, suggesting that a ransomware attack was responsible for the outage. According to those who were at the hospital at the time of the incident, doctors were using cell phones to communicate with staff and paper charts. Both are tasks normally performed by the hospital's computer network.
Ascension is currently investigating the cyberattack and has said some systems remain disrupted.
Ransomware gang extorts NRS Healthcare
Another UK-based ransomware attack was on mobility aid manufacturer NRS Healthcare. More information about this attack came to light this week.
The attack, which took place on March 29, took all NRS Healthcare services offline. The RansomHUB ransomware group turned to the dark web to take responsibility for disabling their phone lines, email, and websites. The group also claimed to have stolen 578GB of data and said that to obtain the decryption key and “resolve” the data breach, NRS Healthcare must contact them “as soon as possible.”
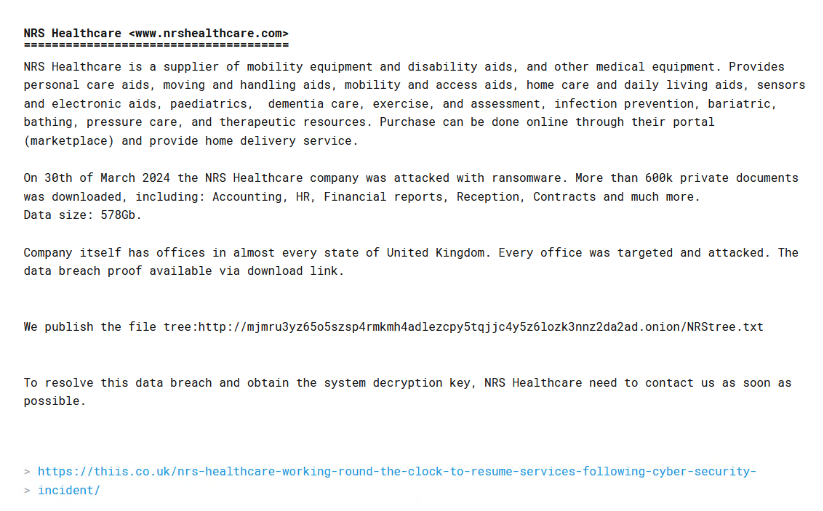
The stolen information allegedly includes more than 600,000 private documents, including contracts, accounting documents and financial reports. While NRS Healthcare currently believes that the information relates only to an internal part of its network, the company acknowledged that information related to customers may have been copied to the internal part of the network and therefore the hackers have accessed it. .
Why have there been so many ransomware attacks in the healthcare sector?
Healthcare organizations have a large number of very important, confidential and sensitive information. This information can range from private medical conditions such as HIV+ status to information on sensitive topics such as abortion and infertility, and confidential information related to criminal cases such as domestic or sexual violence.
Beyond this, healthcare organizations collect and retain a lot of personal patient information, such as home and email addresses, phone numbers, and full names, as it helps them provide services to their patients.
The sensitive and private nature of this information, coupled with the fact that patients will generally not want this information exposed to the general public, make healthcare organizations a perfect target for hackers. By stealing it, encrypting it, and threatening to leak it unless the organization pays a ransom, they put healthcare providers in a really difficult situation.

Either they can go against cybersecurity best practices and pay hackers to protect the information, or they can't pay and leak the data. Of course, there is a third option where the organization pays the hackers, but then the information is leaked anyway; No matter what, these organizations find themselves in a lose-lose position.
That said, this is why implementing good cybersecurity is so important for these healthcare organizations. Take the Change Healthcare cyberattack in February of this year as an example.
Following the attack, it was revealed that the Citrix portal hackers used to infiltrate Change Healthcare's network did not have multi-factor authentication (MFA) enabled and that stolen credentials had been used to gain access to the network.
While the hackers may have been able to gain access to United Healthcare's systems despite this, it could have been the step that slowed them down or alerted the company that they were on the network, potentially mitigating the impact of the cyberattack.