Cyberattackers are using a new strain of ransomware called ShrinkLocker to attack business computers. Take advantage of the Microsoft BitLocker encryption feature to encrypt your entire local drive and remove recovery options before shutting down your PC. ShrinkLocker was discovered by cybersecurity company Kaspersky and analysts have observed variants in Mexico, Indonesia and Jordan.
BitLocker has been used to orchestrate ransomware attacks in the past, but this strain has “previously unreported features to maximize attack damage,” Kaspersky said in a press release. ShrinkLocker is unique in that it can check a device's Windows operating system version to make sure it enables the appropriate BitLocker features, but kills itself if it can't.
Cristian Souza, incident response specialist with Kaspersky's Global Emergency Response Team, said in the press release: “What is particularly concerning about this case is that BitLocker, originally designed to mitigate the risks of data theft or exposure , has been reused by adversaries for malicious purposes. ends. “It is a cruel irony that a security measure has been weaponized in this way.”
Who is vulnerable to the ShrinkLocker attack?
So far, ShrinkLocker has targeted steel and vaccine manufacturing companies, as well as a government entity. However, Souza told TechRepublic that “there is no evidence to believe that this group is targeting specific industries,” as the victims are from different countries and sectors.
BitLocker is currently only available in the Pro, Enterprise, Education, and Ultimate editions of Windows operating systems, but will be included and automatically enabled in all versions with the release of Windows 11 24H2 later this year. This significantly increases the potential reach of ShrinkLocker victims.
“ShrinkLocker infections can be critical if the victim does not have adequate proactive and reactive measures,” Souza added. “Since BitLocker is a native Windows feature, any machine running Windows Vista+ or Server 2008+ could be affected.”
How does ShrinkLocker work?
Although ShrinkLocker erases itself after encrypting the target, Kaspersky analysts were able to discover how it works by studying a script left on a drive of a PC that was infected but did not have BitLocker configured.
Attackers can deploy ShrinkLocker on a device by exploiting unpatched vulnerabilities, stolen credentials, or Internet services to gain access to servers. A user can also download the script inadvertently, for example through a link in a phishing email.
“Once they have access to the target system, the attacker can attempt to exfiltrate information and ultimately run the ransomware to encrypt the data,” Souza told TechRepublic.
Once the script is activated, it uses the Windows Management Instrumentation extensions and the Win32_OperatingSystem class to query information about the device's operating system and domain. If the device is running on Windows XP, 2000, 2003, or Vista, or the current domain of the queried objects does not match the destination, the script deletes itself.
SEE: Is there an easy way to recover BitLocker encrypted drives?
However, if the PC is running Windows 2008 or earlier, the script will move on to resize your local fixed drives. Shrinks non-boot partitions by 100 MB to create unallocated disk space, which is why it has been called ShrinkLocker. New primary partitions are created in the unallocated space and the startup files are reinstalled so that the victim can reboot the system with the encrypted files.
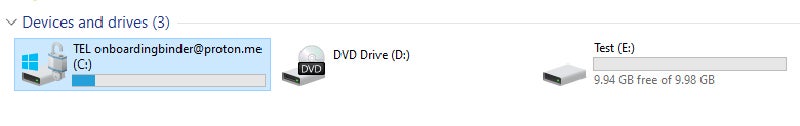
The script then modifies Windows registry entries to disable Remote Desktop Protocol connections and enforce BitLocker settings, such as PIN requirements. Then rename the boot partitions with the attacker's email: onboardingbinder[at]proton[dot]me or conspiracyid9[at]proton mail[dot]com and replaces existing BitLocker key protectors to prevent recovery.
ShrinkLocker creates a new 64-character encryption key by randomly multiplying and replacing the following elements:
- A variable with the numbers zero to nine.
- The pangram “The fast brown fox jumps over the lazy dog”, which contains all the letters of the English alphabet, in lowercase and uppercase.
- Special characters.
Then enable BitLocker encryption on all drives on the device. ShrinkLocker only encrypts the local fixed drive of the infected PC and does not infect network drives that can help evade detection.
The 64-character key and some system information are sent to the attacker's server via an HTTP POST request to a randomly generated subdomain of 'trycloudflare[dot]com.' This is a legitimate CloudFlare domain that is intended to be used by developers to test the CloudFlare Tunnel without adding a site to the CloudFlare DNS. Attackers take advantage of it here to hide their real address.
Finally, ShrinkLocker automatically kills your script and scheduled tasks, clears logs, turns on the firewall, and deletes all rules before forcing shutdown. When the user reboots the device, they are presented with the BitLocker recovery screen with no recovery options available: all data on the PC is encrypted, locked, and out of reach.
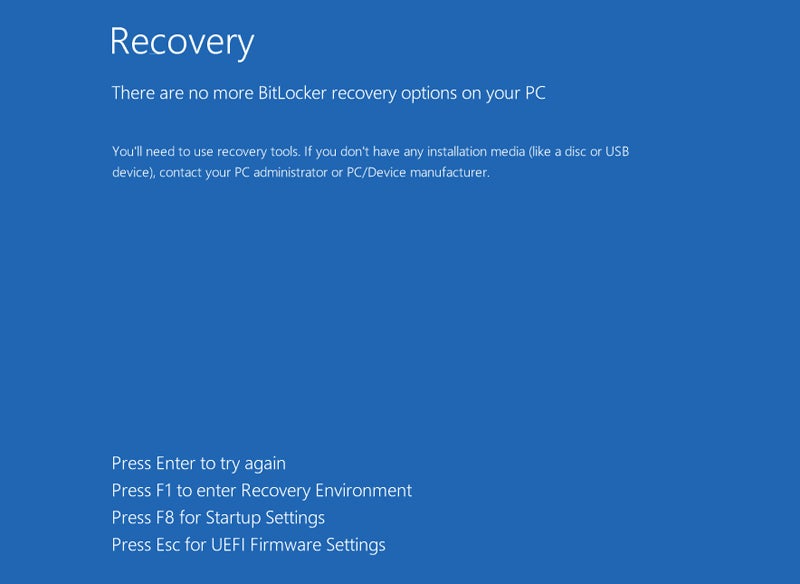
New drive tags with the attacker's email instruct the user to contact them, implying a ransom demand for the decryption key.
In a technical analysis, Kaspersky analysts describe both the detection of a ShrinkLocker attack and the decryption process as “difficult.” The latter is particularly difficult because the malicious script contains different variables for each affected system.
Who is responsible for ShrinkLocker attacks?
So far, Kaspersky experts have been unable to identify the source of the ShrinkLocker attacks or where the decryption keys and other device information are sent. However, some information about the attackers can be obtained from the malware script.
Analysts said the script, written in VBScript, “demonstrates that the malicious actors involved in this attack have excellent knowledge of Windows internals.”
Tags containing the attacker's email address can only be seen if an administrator boots the infected device into a recovery environment or with diagnostic tools, according to BleepingComputer. Additionally, a custom note can be added to the BitLocker recovery screen, but the attackers specifically chose not to create one.
The fact that the attackers appear to have intentionally made contact with them difficult suggests that their motives are disruption and destruction rather than financial gain.
“For now, we know we're dealing with a very capable group,” Souza told TechRepublic. “The malware we were able to analyze shows that the attackers have deep knowledge of the internal components of the operating system and various tools that live off the land.”
How can businesses protect themselves against ShrinkLocker?
Kaspersky offers the following advice to businesses looking to protect their devices from the ShrinkLocker infection:
- Use robust and properly configured endpoint protection platforms to detect possible malicious activities before encryption.
- Implement managed detection and response to proactively scan for threats.
- Make sure BitLocker has a strong password and recovery keys are stored in a secure location.
- Limit user privileges to the minimum necessary to do your job. This way, no unauthorized personnel can enable encryption features or change registry keys on their own.
- Enable logging and monitoring of network trafficcapturing GET and POST requests, as infected systems can transmit passwords or keys to attacking domains.
- Monitor VBScript and PowerShell execution eventssaving logged scripts and commands to an external repository to retain activity even if local logs are deleted.
- Make backups frequentlySave them offline and try them.
How has BitLocker been attacked in the past?
BitLocker has been targeted by bad actors numerous times in the past, long before the emergence of ShrinkLocker. In 2021, a hospital in Belgium had 40 servers and 100TB of its data encrypted after an attacker exploited BitLocker, causing delays in surgeries and redirection of patients to other facilities.
The following year, another attacker targeted one of Russia's largest meat suppliers in the same way, before Microsoft reported that the Iranian government had sponsored a series of BitLocker-based ransomware attacks demanding thousands of US dollars. by the decryption key.












