The Office of the Australian Information Commissioner’s latest Notifiable Data Breach Report revealed a rapid nationwide increase in notifiable data breaches in the first six months of 2024 – a 9% increase compared to the last six months of 2023 and the highest number of notifications since 2020.
The report, released in September, showed that recent data breaches, including the outage of the MediSecure prescription service that affected 12.9 million Australians, have prompted a strong response from the OAIC. The agency warned that it is taking a tougher stance on data privacy and breaches, and stressed that organisations must prioritise privacy in their data practices.
Which industries experienced the most data breaches?
The OAIC has published statistical information on data breach notifications since the launch of the Notifiable Data Breaches scheme in Australia in 2018. The latest report revealed:
- In total, 527 notifications were made between January and June 2024, which represents an increase of 9% compared to the 485 notifications received between July and December 2023.
- The last six months saw the highest number of notifications received since July to December 2020, at the height of the global COVID-19 pandemic.
- The top five sectors that suffered data breaches were healthcare providers (102 breaches), the Australian Government (63), finance (58), education (44) and retail (29).
- Malicious or criminal attacks, both external and internal, were the source of 67% of all data breaches, followed by human error (30%) and system failures (3%).
- Malicious or criminal attacks included cyber incidents (57%), social engineering/phishing (27%), theft of documents or data storage (8%), and insider or rogue employee threats (8%).
- The majority of reported breaches (63%) affected 100 people or fewer, but there were eight large-scale breaches affecting more than 100,000 people, including Australia’s “largest ever” MediSecure breach.
SEE: Australian organisations experience highest rate of data breaches
Cyber incidents dominate malicious and criminal attacks in Australia
Cyber incidents remain a common cause of data breaches, accounting for 38% of all breaches. Cyber incidents were defined as those involving phishing, ransomware, compromised or stolen credentials (method unknown), brute force attacks, hacking, and malware, but not social engineering attacks.
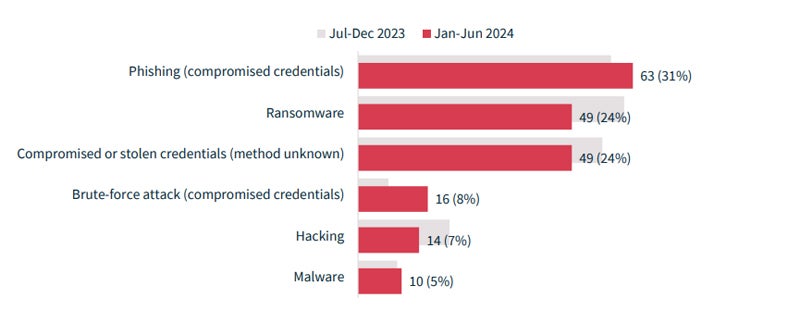
Among the various malicious or criminal attacks, cyber incidents had the greatest impact on people. An average of 107,123 people were affected by the 201 cyber incidents, while an average of 4,709 people were affected by incidents caused by rogue employees or insider threats.
In the report, Australian Privacy Commissioner Carly Kind said the continued prevalence of cyber incidents in data breach totals reported to the OAIC came “as our increasing reliance on digital tools and online services exposes our data more frequently to malicious cyber actors.”
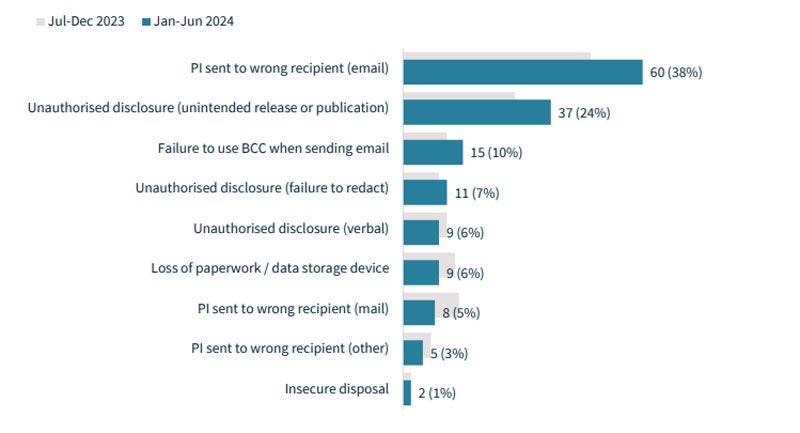
However, human error is still responsible for 30% of reportable data breaches. The top categories of human error were:
- Personally identifiable information sent to the wrong email recipient (38%).
- Unauthorized disclosure of information, or unintentional publication or disclosure (24%).
- Do not use the BCC (Blind Carbon Copy) option when sending email (10%).
Rising data breaches put Australian government agencies in the spotlight
The OAIC noted that the Australian government recorded the second highest number of data breaches of any sector, its highest ranking ever, although it was previously among the top five sectors with the highest number of breaches. According to the report:
- Government agencies reported 63 data breaches between January and June 2024, representing 12% of all data breach notifications in Australia.
- The government was responsible for the largest number of data breaches involving social engineering or phishing, accounting for 42% of those incidents. According to the OAIC, these breaches typically involved a threat actor impersonating a customer to gain access to an account using legitimate credentials.
- The government is also slower to act: it had the highest proportion (87%) of notifications where the agency identified the incident more than 30 days after it occurred, while 78% of government notifications were made more than 30 days after the agency became aware of the incident.
WATCH: Is Australia's public sector prepared for a major cybersecurity incident?
How can organizations stop data breaches?
Security experts are constantly reminding organizations that many data breaches or cyberattacks could be prevented by implementing basic cybersecurity measures. The OAIC has put forward several recommendations based on trends in data breach data.
Cyber Threat Mitigation
The OAIC recommended implementing multi-factor authentication as a first priority to stop cyber threats, or strong password management policies and practices if multi-factor authentication is not available. The agency also recommended:
- Implement layered security controls to prevent a single point of failure.
- Impose levels of access to information based on roles and responsibilities.
- Leverage security monitoring to detect, respond to, and report incidents or unusual activities.
The OAIC highlighted frameworks such as Australia's Essential Eight, the Australian Signals Directorate's Information Security Handbook, the US-based National Institute of Standards and Technology's Cyber Security Framework, and the International Organization for Standardization's ISO 27001 and ISO 27002 information security management standards as guiding practice improvements.
Extended Supply Chain Risks
According to the OAIC, some large-scale data breaches are due to supply chain violations, such as the one affecting MediSecure and another incident involving Outabox. The agency added that outsourcing the handling of personal information to third parties remains a frequent risk.
The agency said companies should consider the risks of outsourcing the handling of personal information at the earliest stage of engagement, including to cloud service providers. It also recommended that organisations establish a robust risk management framework for suppliers, along with stronger security measures.
Addressing the human factor
The OAIC highlighted that individuals remain a significant threat to the soundness of privacy practices. These threats include breaches due to human error or employees being tricked through phishing.
The agency urged organizations to implement technical measures to reduce errors and stressed that it is essential to train staff to ensure they understand their privacy and security obligations. It also recommended prioritizing staff training on secure information handling practices.
Incorrect configuration of cloud-based data warehouses
Some organisations are “overlooking” cloud security as they digitally transform, the OAIC said. Several data breaches during the quarter occurred when an Australian entity incorrectly configured security settings due to human error, leaving personal information vulnerable to unauthorised access or public disclosure.
The OAIC said organisations should not assume that responsibility for cloud security lies with the provider. The agency noted that cloud security and management should be a priority, highlighting the importance of measures such as secure access controls using MFA, IP access controls and encryption.











