A new report from IBM X-Force exposes changes in the Grandoreiro malware landscape. The banking trojan is now capable of attacking more than 1,500 global banks in more than 60 countries and has been updated with new features.
Additionally, Grandoreiro's target has become broader, as it initially only targeted Spanish-speaking countries, while recent attack campaigns targeted countries in Europe, Asia, and Africa. Additionally, the malware now sends phishing emails directly from the victim's local Microsoft Outlook client to recipient email addresses located on the local system.
What is Grandoreiro?
According to Interpol, the Grandoreiro banking trojan has been a major threat in Spanish-speaking countries since 2017. The main functionalities of the malware allow cybercriminals to control devices on the infected computer, enable keylogging, manage windows and processes, open a browser and run JavaScript inside. download it, upload or download files and send emails, in addition to its banking Trojan capabilities.
Analysis of different attack campaigns reveals that many operators are involved in Grandoreiro attacks, as stated by cybersecurity company Kaspersky, writing in July 2020: “It is not yet possible to link this malware to any specific cybercrime group, although It is clear that the campaign uses a MaaS (Malware-as-a-Service) business model.”
SEE: Kaspersky study: Devices infected with data-stealing malware have increased 7-fold since 2020
Arrests of suspected cybercriminals in connection with Grandoreiro occurred in 2021, with Spanish police arresting 16 suspects accused of laundering stolen funds through two banking Trojans, including Grandoreiro. More recently, Brazilian authorities arrested five programmers and administrators behind the banking malware, suspected of having defrauded victims of more than 3.5 million euros.
However, the malware, developed in Brazil, is still active and has begun to expand its target list to other countries, including Japan, the Netherlands, Italy and South Africa, as reported in new research from IBM's X-Force team. .
How do Grandoreiro campaigns work?
All Grandoreiro campaigns start with phishing emails
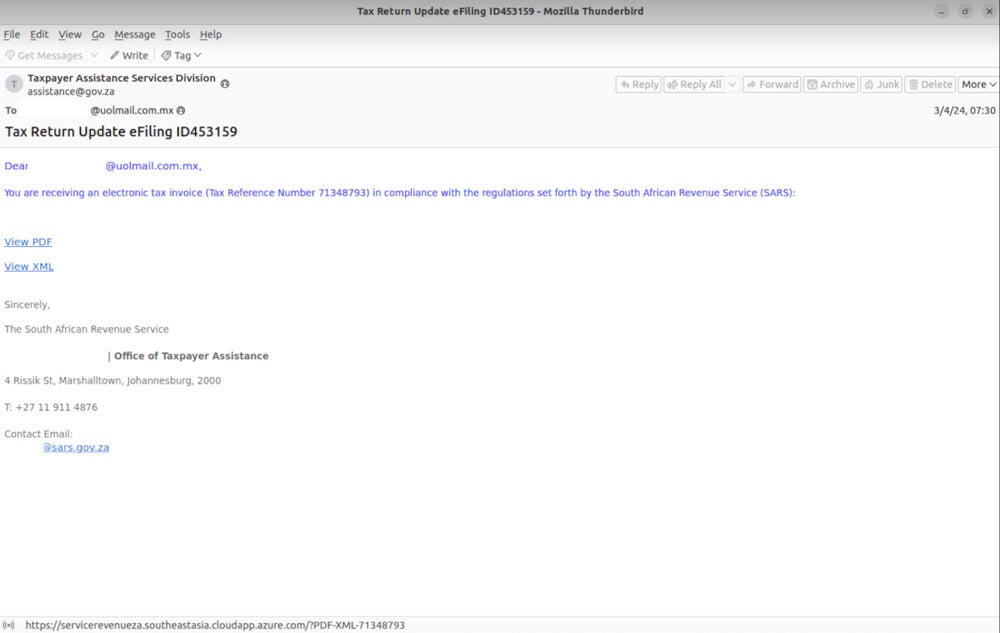
Since March 2024, several Grandoreiro phishing campaigns have impersonated entities in Mexico, such as the Mexican Tax Administration Service, the Mexican Federal Electricity Commission or the Argentine Tax Service.
Since March 2024, different social engineering techniques have been used in emails to encourage the user to click on a link: a final notice to pay a debt, a reminder that you can access your account statement in PDF or XML format or a reminder to read the details. in a compliance notice.
In those phishing campaigns, only users coming from specific countries (Mexico, Chile, Spain, Costa Rica, Peru, Argentina) are redirected to a payload upon clicking the link provided in the email.
Following recent arrests involving Grandoreiro operators, researchers saw an increase in campaigns targeting countries beyond the usual Spanish-speaking ones, including Japan, the Netherlands, Italy and South Africa, with emails written in English.
Then comes the chain of infection.
After the user clicks on the malicious link in the phishing email, a custom loader is launched that presents a fake Adobe PDF Reader captcha, which requires a click to continue execution, probably to distinguish between real users and automated systems such as sandboxes.
The loader then collects some data from the victim and sends it to the command and control server using encryption based on AES and base64 algorithms. The data sent to C2 consists of the computer and user names, the operating system version, the antivirus name, the victim's public IP address, and a list of running processes. In addition, the loader checks for the existence of the Microsoft Outlook client, as well as crypto wallets and special banking security products such as IBM Trusteer or Topaz OFD.
The uploader can be configured to not allow victims from specific countries based on their IP addresses. A malware sample found by IBM X-Force stopped if the user was located in Russia, the Czech Republic, Poland or the Netherlands.
If all conditions are met, the Grandoreiro banking trojan is downloaded, decrypted using an RC4-based algorithm and executed.
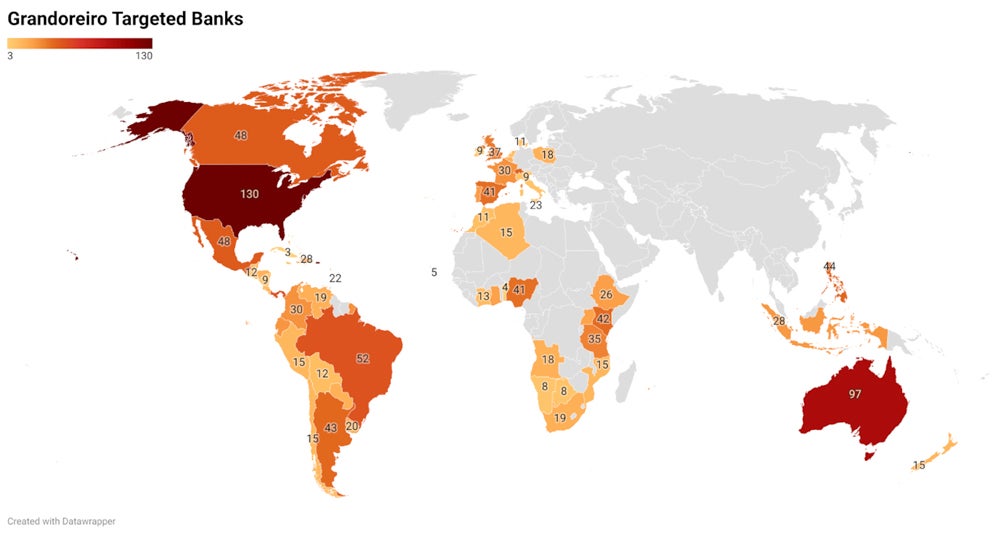
Aimed at more than 1,500 banks worldwide
The list of Grandoreiro-specific applications has grown to more than 1,500 banks worldwide, according to IBM X-Force, and banking applications are also tied to regions. For example, if the victim's country is identified as Belgium, the malware will search for all banking applications associated with the European region.
Additionally, the malware uses 266 unique strings to identify cryptocurrency wallets.
Recent updates in Grandoreiro
New DGA algorithm
Researchers Golo Mühr and Melissa Frydrych analyzed the malware in depth and discovered that the malware, which traditionally relied on domain generation algorithms to find its C2 server references, contained a reworked DGA.
The new algorithm introduces multiple seeds for its DGA, “used to calculate a different domain for each mode or functionality of the banking Trojan, allowing the separation of C2 tasks between multiple operators as part of its Malware-as-a-Service operation,” as it is stated. by the researchers.
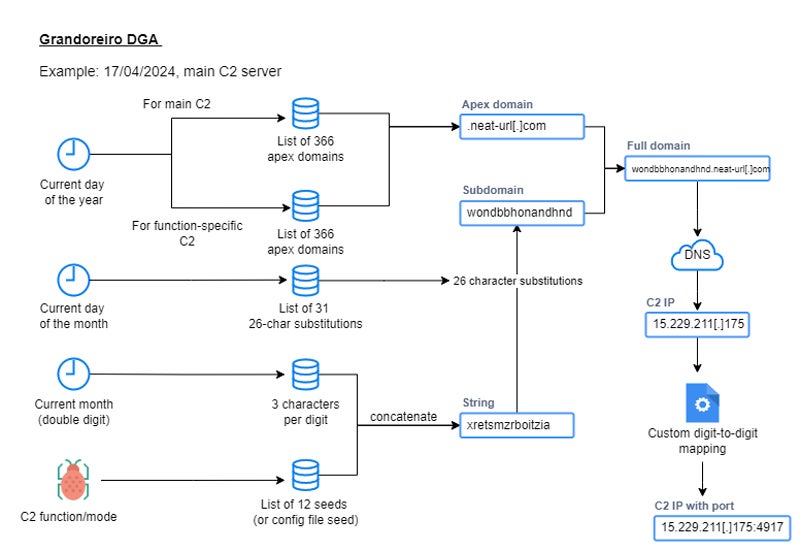
For a sample analyzed, for a given day, 12 domains could be used as C2 domains, four of which would be active that day and lead to IP addresses based in Brazil.
Microsoft Outlook Abuse
Recent versions of Grandoreiro abuse local Microsoft Outlook software when it is available on an infected computer.
The malware interacts with Outlook Security Manager Tool, a tool designed to develop Outlook add-ins. Using the tool allows the malware to disable alerts within Outlook before beginning to collect all sender email addresses found in the victim's mailbox, filtering email addresses to avoid collecting unwanted addresses, such as those that contain “noreply”, “feedback” or “newsletter”. ”, to name a few from the malware blocking list.
Additionally, the malware recursively scans parts of the victim's folders to search for more email addresses, looking for files with specific extensions, including .csv, .txt, .xls, and .doc.
The malware then starts sending spam based on phishing templates it received from its C2 server before deleting all sent emails from the victim's mailbox.
To avoid being caught by the user who might notice suspicious behavior on the computer, the malware only starts sending emails when the last entry on the machine is at least five minutes old or longer in some malware variants.
How to protect yourself from this Grandoreiro malware threat
- Do a careful analysis of the network. In particular, multiple consecutive requests to ip-api.com/json should trigger alerts and investigations, as they could be an indicator of a Grandoreiro infection.
- Monitor execution keys in the Windows registry. Any addition outside of a normal software installation should be closely investigated for malware activity.
- Block pre-calculated DGA domains via DNS.
- Deploy endpoint security software on each computer to detect malware.
- Educate users and staff to detect phishing emails and potential fraud attempts.
- Keep all hardware and software updated and patched to avoid becoming infected through a common vulnerability.
Divulgation: I work for Trend Micro, but the opinions expressed in this article are my own.