Highlights from CrowdStrike's 2024 report:
|
CrowdStrike's new Global Threat 2024 report lays out the latest trends in cyberattacks and highlights the top topics of interest to businesses.
The cyberattack ecosystem continues to grow, with CrowdStrike seeing 34 new threat actors in 2023. Attackers are increasingly targeting cloud environments, primarily for financial reasons. However, in some cases, it allows attackers to reach local servers.
Supply chain attacks are often used as they allow a threat actor to hit multiple targets easily. Organizations operating in the technology sector are also at unique risk from such attacks, as nearly all compromises in trusted relationships originated from intrusions into organizations that provide commercial software. End-of-life products and unmanaged devices at the edge of the network are also targeted.
1. Social engineering and identity-based attacks continue to take center stage.
While phishing remains a valid method of obtaining employee credentials from specific organizations, other authentication data is also used to conduct attacks. Regardless of the motivation for a cybersecurity attack, social engineering and identity-based attacks continue to take center stage.
For example, threat actor FANCY BEAR ran phishing campaigns in 2023 and developed a custom toolset to harvest Yahoo! credentials. ukr.net email and webmail users. The toolkit used the Browser-in-Browser technique and added multi-factor authentication interception capabilities to collect one-time passwords used in authentication.
SCATTERED SPIDER used SMS phishing (smishing) and voice phishing (vishing) to obtain credentials. And the threat actor leveraged previous intrusions into telecom organizations to execute SIM swap operations on targeted employees; Once SIM swapping is active, the threat actor could receive SMS messages with OTP codes directly. Additionally, the threat actor often used residential proxies to avoid detections based on the physical location of their target.
Attackers also target API keys and secrets: possessing them allows a cybercriminal to maintain access indefinitely as long as the API keys or secrets are not modified. Threat actors also used cookie sessions and token theft in 2023.
Additionally, attackers steal or forge Kerberos tickets to gain access to encrypted credentials that can be decrypted offline. CrowdStrike has seen a whopping 583% increase in Kerberoasting attacks.
2. Intrusions into the cloud environment increased by 75%.
CrowdStrike noted that intrusions into the cloud environment have increased globally by 75% between 2022 and 2023 (Figure A).
In CrowdStrike's analysis, the team separates cloud-aware cases (i.e. cases where the attacker is aware of and makes use of the cloud environment) and cloud-agnostic cases (i.e. a attacker does not notice the cloud environment or does not use it).
Cloud-related cases increased 110%, while cloud-independent cases increased 60% from 2022 to 2023.
Financially motivated cybercriminals are the most active when it comes to attacking cloud environments; They are responsible for 84% of all cloud intrusions, while targeted intrusions only account for 16%.
Attackers could take advantage of intrusions into the cloud environment to attack corporate networks. As an example, the SCATTERED SPIDER threat actor often uses the victim's Microsoft 365 environments to scan for VPN instructions before using the VPN to access and move laterally within the target organization's internal network.
3. Exploiting third-party relationships makes it easier for attackers to hit hundreds of targets.
According to the CrowdStrike report, targeted intrusion actors consistently attempted to exploit trusted relationships to gain access to organizations across multiple verticals and regions in 2023.
Such attacks have an interesting return on investment for attackers: Compromising a third party that provides IT services or a third party that is part of a software supply chain can result in hundreds or thousands of tracking targets. Such attacks can also more effectively help attackers targeting a strengthened organization.
For example, JACKPOT PANDA used a Trojanized installer for CloudChat, a popular China-based chat app often used by gaming communities, which ultimately infected users with malware called XShade.
In another case, an unidentified threat actor compromised an India-based information security software vendor to distribute malware through the legitimate software update process.
According to CrowdStrike, compromises in trust relationships will continue to attract specific intrusion actors for the foreseeable future. Organizations operating in the technology sector are at greater risk because they provide their services to many organizations around the world.
4. CrowdStrike added 34 new threat actors in 2023.
Over the course of 2023, CrowdStrike added 34 new threat actors, also called adversaries, to its list of 232 actors. In addition to these known adversaries, CrowdStrike tracks more than 130 groups of active and malicious activity.
Sites dedicated to data breaches showed a 76% increase from 2022 in the number of exposed victims, bringing the total victim count to 4,615 by 2023. Newly emerged big game hunting players are one of the factors that increased the number of victims, in addition to the growth of existing adversary operations and high-volume campaigns, such as multiple Graceful Spider threat actor operations. This threat actor exploited three zero-day vulnerabilities to collect data from hundreds of victims around the world.
5. Attackers are compromising networks at a faster rate.
Gaining an initial foothold in a target network is typically only the first phase of an attack; Once inside, attackers must exit the first compromised device and move laterally to other parts of the network to achieve their objectives.
The average breakout time for interactive electronic crime intrusion activity decreased from 84 minutes to 62 minutes between 2022 and 2023, with the fastest breakout time being 2 minutes and 7 seconds.
In an example provided by CrowdStrike, an attacker discarded legitimate tools 31 seconds after the login intrusion began to execute a reconnaissance operation on the network and obtain system information. The attacker then dropped additional files and more tools were added within 3 minutes, including ransomware (Figure B).
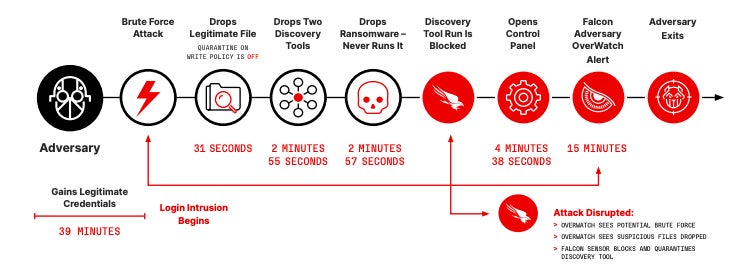
According to the report, attackers also gain time by using less malware and more effective means, such as using stolen credentials and exploiting vulnerabilities in trust relationships. Malware-free activities now account for 75% of all detections in 2023, compared to 71% in 2022 and less than 62% before 2021. The success of identity attacks and the purchase of valid credentials from intermediaries initial access explain this tendency to use less malware.
6. Attackers target peripheral networks.
Due to the increased use of response sensors and endpoint detection, threat actors have adapted their exploitation tactics for initial access and lateral movements targeting the network periphery (Figure C).
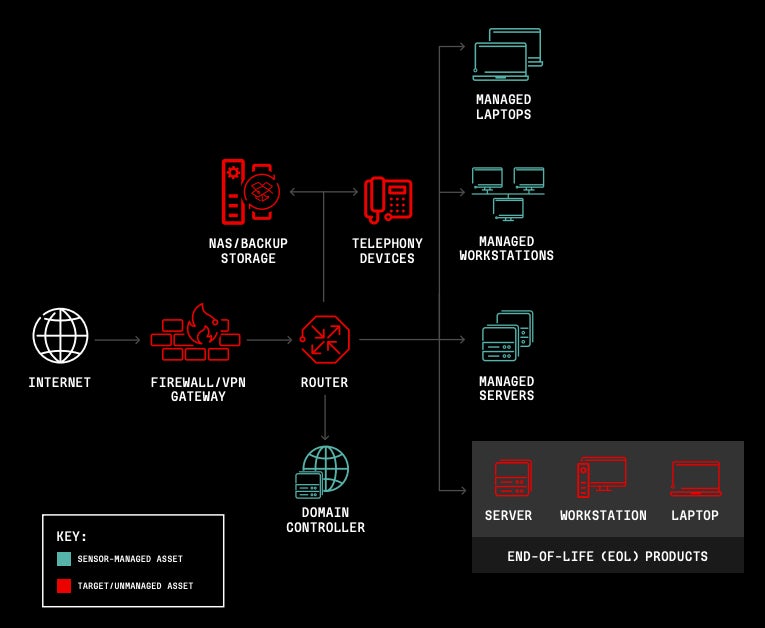
Some devices are not necessarily monitored by security solutions within a corporate network. In particular, edge gateway devices are often based on outdated architecture and are therefore vulnerable to several vulnerabilities that could be exploited by attackers.
Vulnerabilities in firewalls and VPN platforms affected, for example, Cisco, Citrix and F5 in 2023. Routers, mobile phones or NAS/backup storage could also be affected.
CrowdStrike highlighted another trend seen in 2023: attacker focus on exploiting end-of-life products. These products, which are no longer patched and often do not support the implementation of modern security solutions, are targeted by attackers who actively develop exploits to abuse these products.
SEE: Routers targeting botnet attacks: A wake-up call to protect remote employee hardware
Recommendations to mitigate these cybersecurity risks
According to CrowdStrike, it is essential to implement phishing-resistant MFA and extend it to protocols and legacies, in addition to educating teams on social engineering.
User awareness programs should be initiated to understand and combat phishing and social engineering techniques.
Technology must be deployed that can detect and correlate threats across identity, endpoint, and cloud environments.
Cloud-native application protection platforms that include pre-execution protection, runtime protection, and agentless technology should be preferred over isolated cloud security tools that do not provide a unified platform for monitoring and detection. possible threats and vulnerabilities.
Since attackers tend to use less malware and use valid credentials and legitimate tools, it is difficult for defenders to differentiate between normal user activity and that of the attacker; Understanding the relationships between identity, cloud, endpoints, and data protection telemetry is mandatory for that task. A consolidated security platform must be implemented that provides complete visibility in one place.
Additionally, advocates should prioritize patching exposed products and removing EOL products.
Disclosure: I work for Trend Micro, but the opinions expressed in this article are my own.












