A joint cybersecurity advisory from the Federal Bureau of Investigation, the Cybersecurity and Infrastructure Security Agency, the Department of Health and Human Services, and the Multistate Information Sharing and Analysis Center was recently released to provide more information about Black Basta ransomware. .
Black Basta affiliates have targeted organizations in the United States, Canada, Japan, the United Kingdom, Australia and New Zealand. As of May 2024, these affiliates have impacted more than 500 organizations worldwide and stolen data from at least 12 of 16 critical infrastructure sectors, according to the joint advisory.
Recent security research indicates that ransomware threats remain high and that more and more companies are paying ransom demands to recover their data.
What is Basta Negro?
Black Basta is a ransomware-as-a-service whose first variants were discovered in April 2022. According to cybersecurity company SentinelOne, Black Basta is most likely linked to FIN7, a threat actor also known as “Carbanak”, active since 2012 and affiliated with several ransomware operations.
Rumors have also spread that Black Basta could have emerged from the old Conti ransomware structure, but cybersecurity company Kaspersky analyzed both codes and found no overlap. The rumors are mainly based on similarities in the modus operandi of Conti and Black Basta, but without solid evidence.
How do Black Basta affiliates operate?
Black Basta affiliates use common techniques to compromise their target's network: phishing, exploiting known vulnerabilities, or purchasing valid credentials from Initial Access Brokers. Black Basta was implemented in systems through the infamous QakBot.
Once inside the network, affiliates use a variety of tools to move laterally through the target network to steal sensitive content and then deploy ransomware (double extortion model). Common management or penetration testing tools are used to perform this task, such as Cobalt Strike, Mimikatz, PsExec or SoftPerfect, to name a few.
A variant of Black Basta also targets Linux-based VMware ESXi virtual machines. The variant encrypts all files in the /vmfs/volumes folder that stores all files on ESXi virtual machines, leaving a ransom note after encryption.
Once the ransomware has been deployed, a ransom note is distributed on the systems. The ransom note contains a unique identifier that the organization needs to contact the cybercriminal via a Tor link.
A countdown begins on the Black Basta Tor site, exposing the names of the companies and information about the data held by Black Basta. Once the timer reaches zero, the stolen data is shared.
The State of Ransomware: Key Trends, Including Ransom Payments
Black Basta ranked 12th most active family of 2023
According to Kaspersky in its latest findings on the state of ransomware in 2024, Black Basta is the 12th most active ransomware family in 2023, with a 71% increase in the number of victims in 2023 compared to 2022.
Kaspersky's incident response team reports that one in three security incidents in 2023 was related to ransomware.
SEE: In 2022, Black Basta was considered one of the most dangerous and destructive ransomware groups
Additionally, researchers noted another important trend observed in 2023: attacks through contractors and service providers, including IT services, became one of the top three attack vectors for the first time. These types of attacks allow cybercriminals to spend less effort on initial compromise and lateral movements and often go undetected until systems are encrypted.
More organizations paid the ransom in 2023
Cybersecurity firm Sophos, in its annual State of Ransomware survey, noted that for the first time, more than half (56%) of organizations that had fallen victim to ransomware admitted they paid the ransom to recover their data in 2023. .
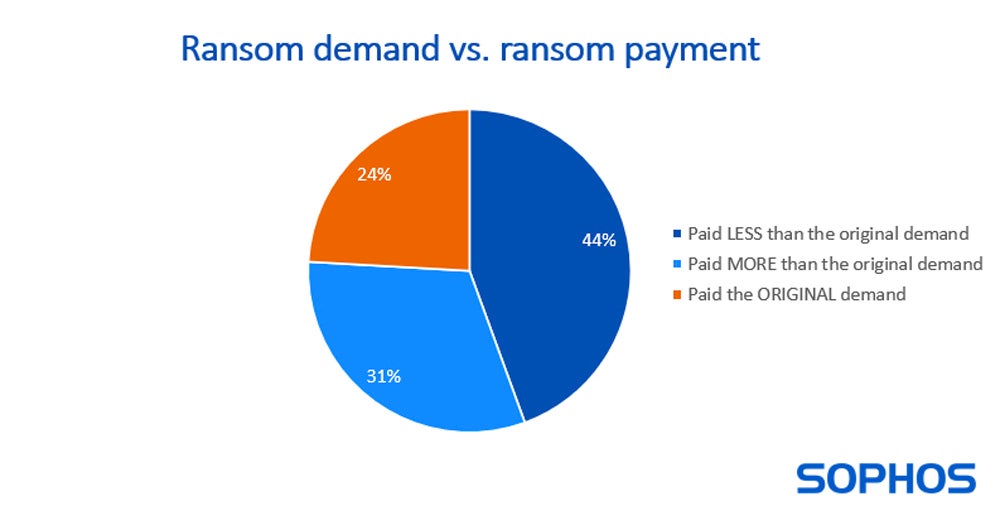
Of the organizations that decided to pay, 44% paid less than the original ransom amount, while 31% paid more.
How to mitigate this Black Basta ransomware threat
CISA's recommendations to all critical infrastructure organizations are as follows:
- Operating system, software, and firmware updates should be installed as soon as they are released.
- Phishing-resistant multi-factor authentication should be required for as many services as possible.
- Awareness must be created; Users must be trained to recognize and report phishing attempts.
- Remote access software must be protected and monitored. In particular, network administrators and defenders must be able to recognize abnormal behavior and detect malicious use of that software.
- Wherever possible, zero trust solutions should be used. The principle of least privilege use should be applied when this is not possible.
- Inactive or obsolete accounts in Active Directory should be audited.
- Safeguards must be used for mass script creation, in addition to a script approval process. An account that attempts to send commands on multiple devices within a certain period of time should see its security protocols, such as MFA, reactivated to ensure the source is legitimate.
- Backups of critical systems and device configuration should be performed frequently to allow devices to be repaired and restored.
- Modern anti-malware software should be used, with automatic signature updates where possible.
- It is strongly recommended to exercise, test and validate the organization's security program against threat behaviors mapped to the MITER ATT&CK for Enterprise framework in the joint assessment.
More mitigation techniques are available in CISA's #StopRansomware Guide.
Divulgation: I work for Trend Micro, but the opinions expressed in this article are my own.











